Configuring Cross Account IAM Role Support for Amazon SQS Snaps
Prerequisites
- Familiarity with the SnapLogic and AWS platforms.
- AWS Account with S3 buckets.
Key Steps
-
Create a Cross Account IAM Role and Policy in AWS Account.
-
Associate the IAM Policy with the Created Role.
-
Configure SQS Account in SnapLogic.
Create a Cross Account IAM Role and Policy in AWS Account
Cross Account IAM Role enables a client from an AWS account to access the resources of another AWS account temporarily using the Binary Snaps that support reading from/writing into S3 buckets. This helps organizations or various teams in an organization to access each other's AWS account without compromising security by sharing AWS credentials.
You can briefly allow access to your AWS account and specify the access duration. You must create a role and policy in your AWS account. The policy created by the host is attached to the access seeker's account. This cross account IAM role enables SnapLogic to trigger the necessary APIs.
Steps
- Log in to the AWS Management Console and navigate to IAM >
Roles.
- Click Create role > Another AWS Account. Specify the account ID for the
other account, that will access your account.
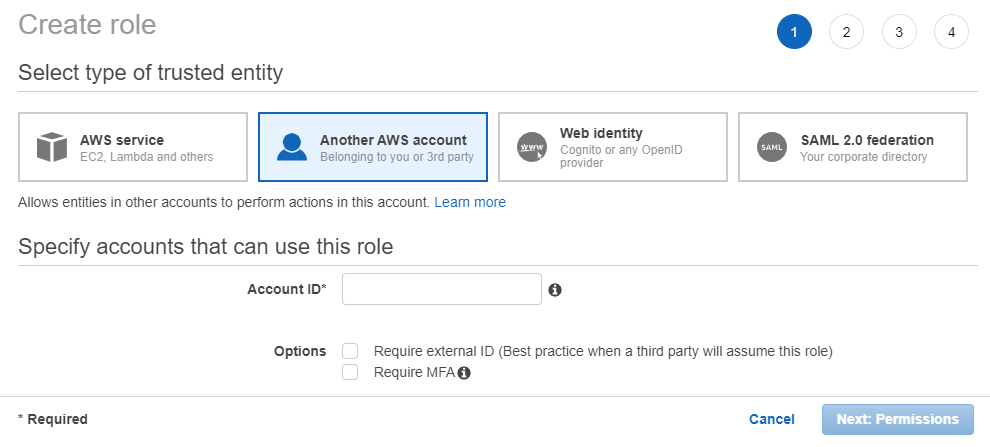
- Enter the account number of the access seeker in the Account ID field, which is
available in the Support Center. Optional. Select Options checkbox to add a
security layer to authenticate for each Login.

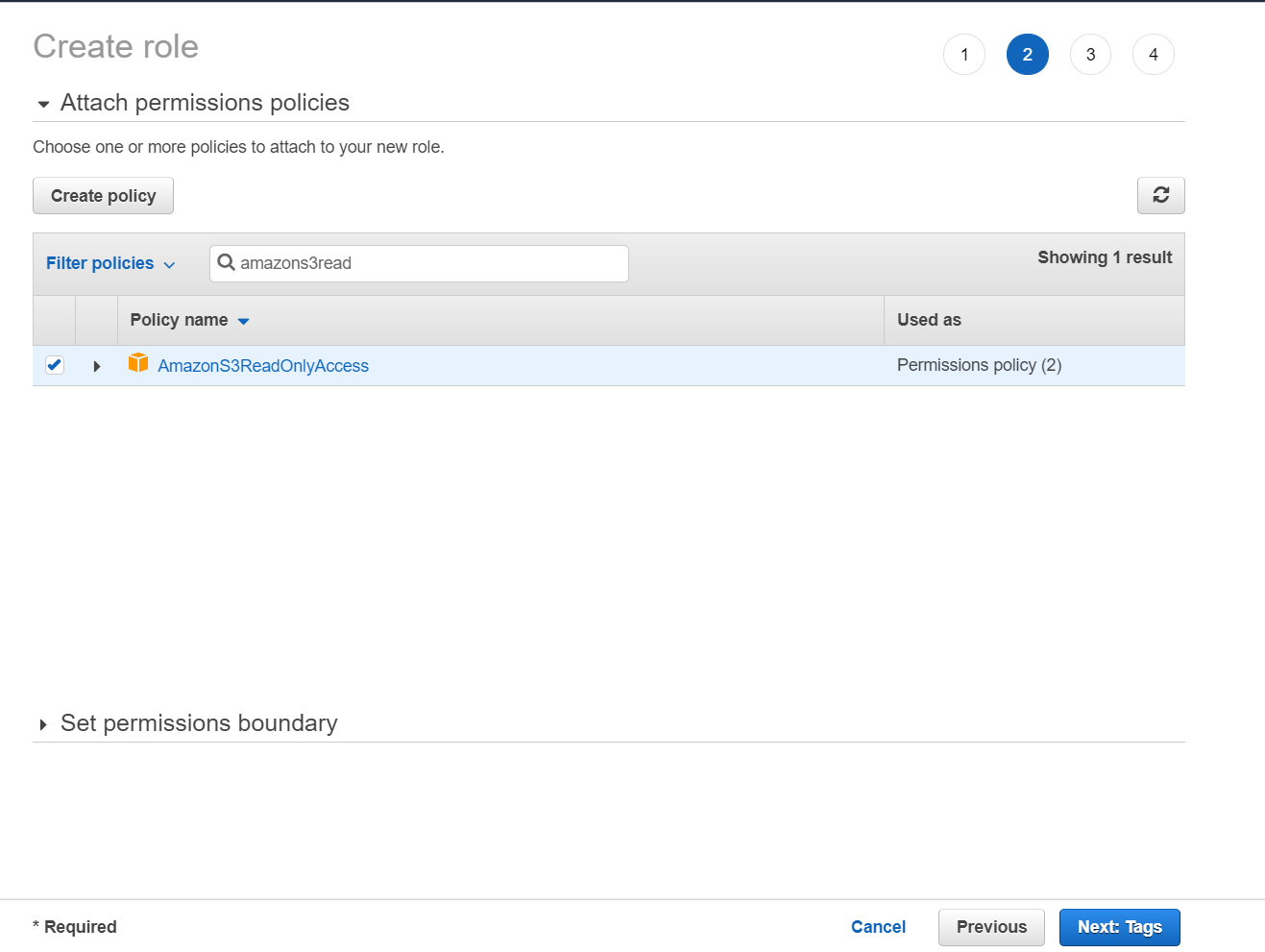
- Click Next: Permissions. The Attach permissions policies screen displays,
where you can set the permissions. Select the check box adjacent to the applicable policy
for the current role.
- Optional Click Next: Tags. Add tags as appropriate.
- Click Next: Review to skip to the next screen.
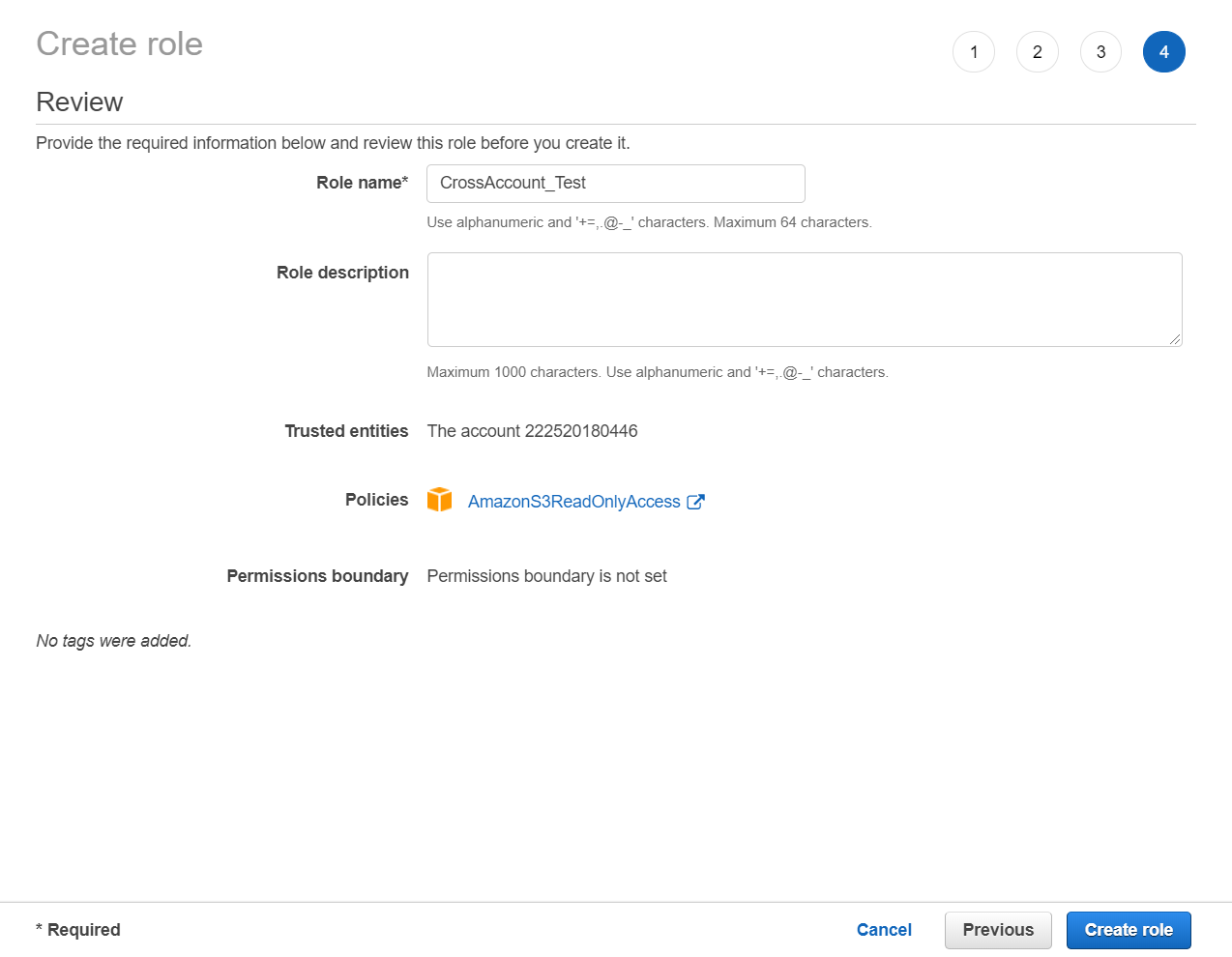
- Review the information, add a name for the role, and click Create role.
- The Summary page displays the Amazon Resource Name number. Make a note of this ARN, as you will need it when completing the AWS IAM Role account settings.
Associate the IAM Policy with the Created Role
Steps
- In your AWS console, click Users and select the User name to associate the
IAM Policy.
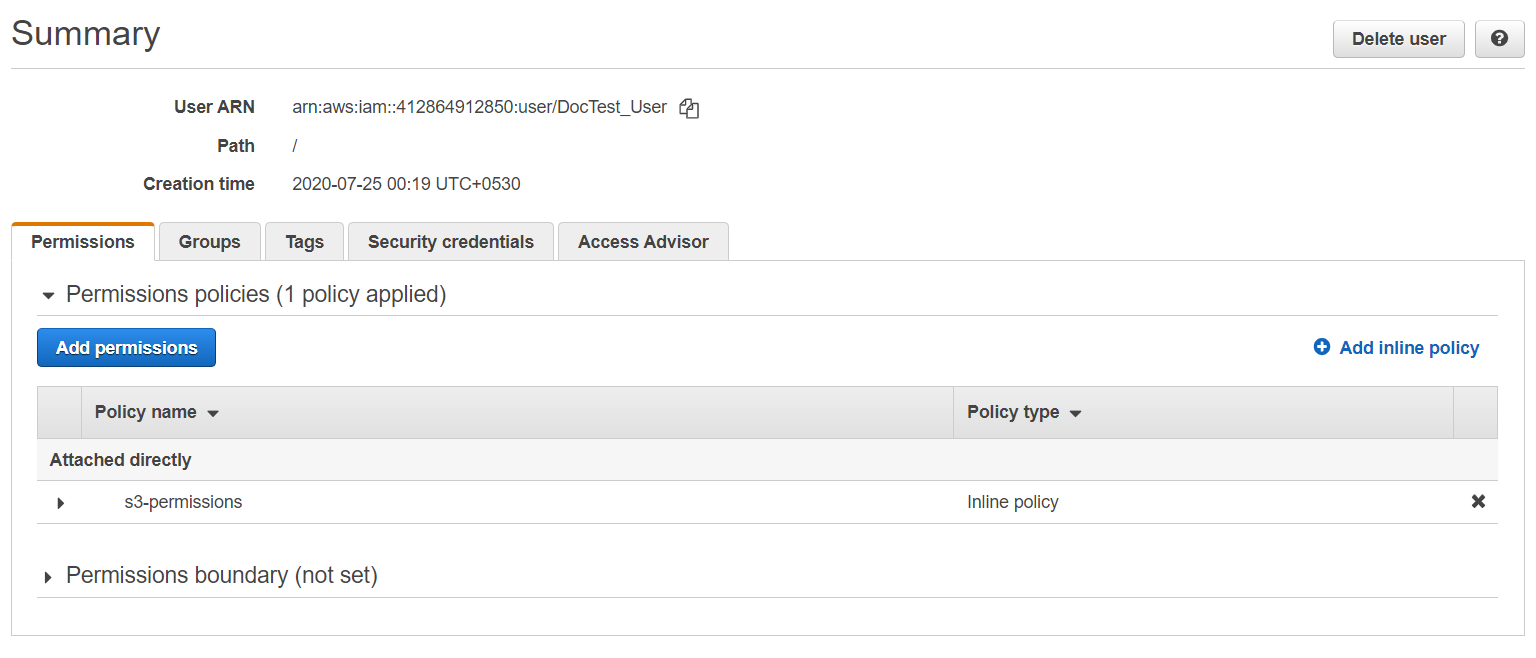
- In the Summary screen, click Add inline policy to attach the
policy.
- Click the JSON tab and enter the following policy in the editor, and then click
Review policy.
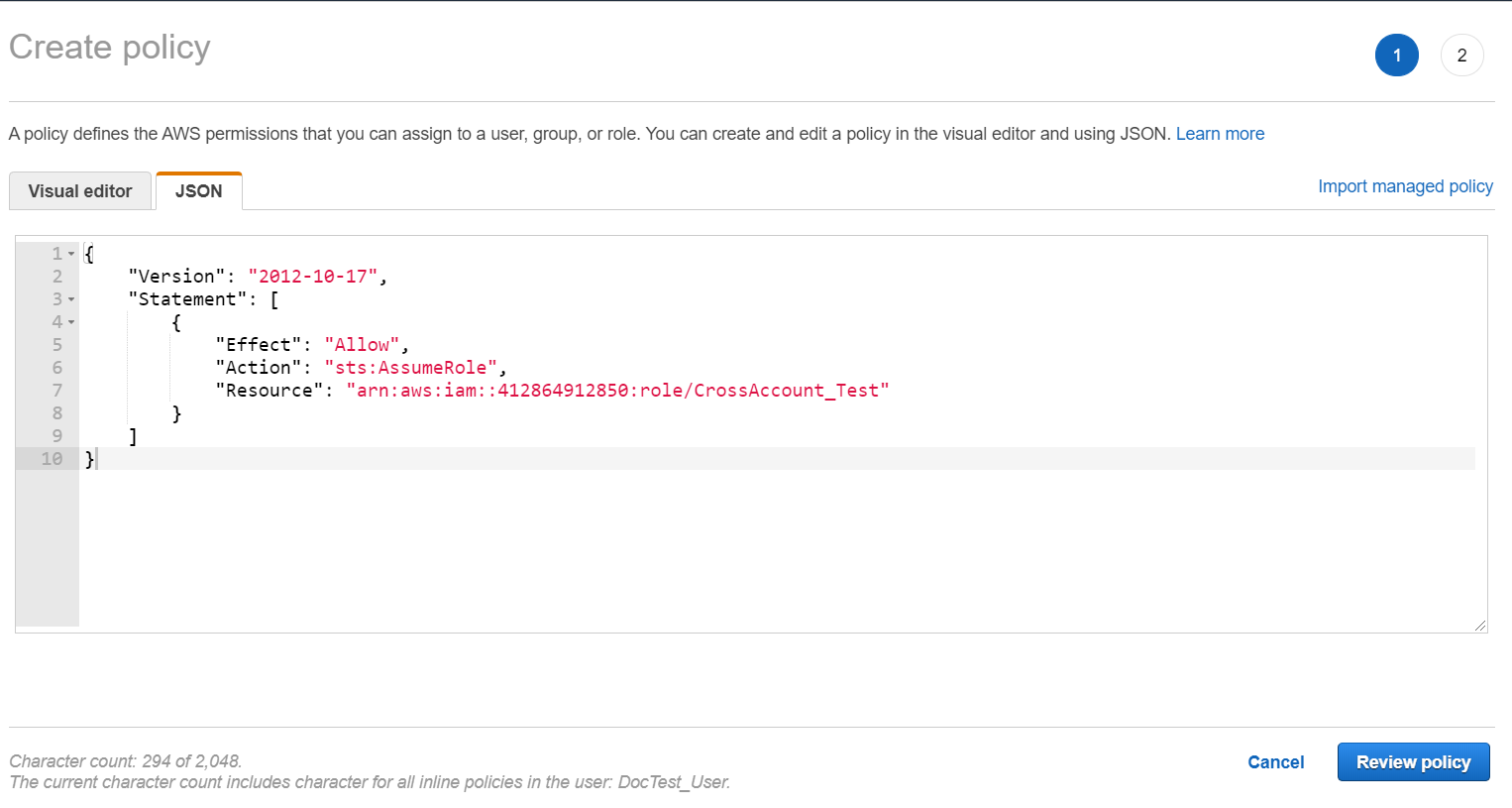
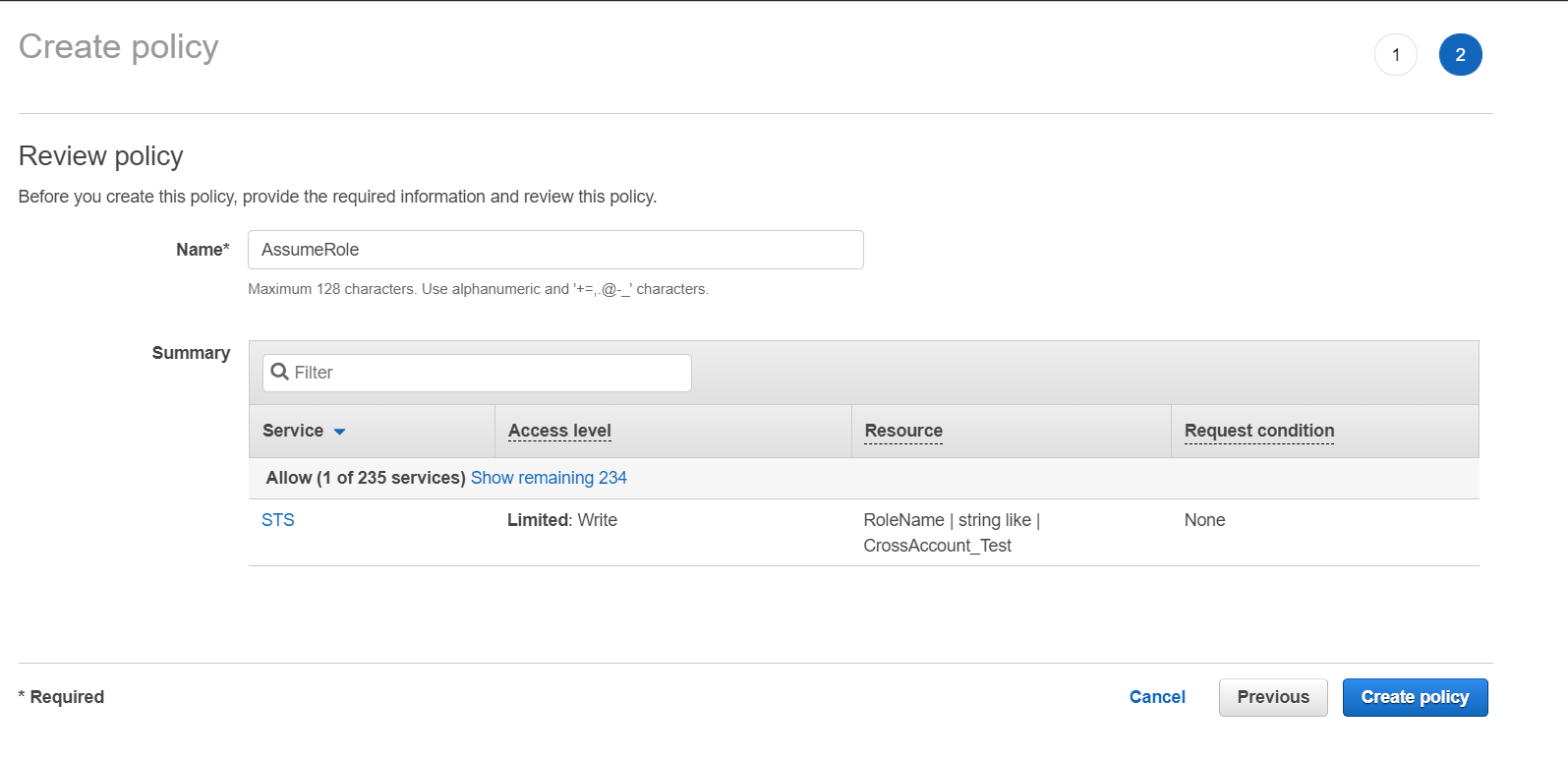
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Action": "sts:AssumeRole", "Resource": "<Role ARN>" } ] } - Review the policy summary. Add a name and optionally, a description for this policy, and
click Create policy.
Configure SQS Account in SnapLogic
You can configure the cross account IAM Role in Amazon SQS Account. Enter the credentials provided for the IAM role. Enter Role ARN and External ID (if setup by the host) provided from the host S3 account.
Steps
- Enter the Access-Key ID, Secret key of the host S3 account. The credentials should belong to the IAM user to whom you have attached a policy previously.
- Enter the Role ARN and External ID provided by the S3 host account.

- For an account used in EC2 groundplex with IAM role configured, select the IAM role check box.
- Enter the Role ARN and External ID provided by the S3 host account.



