Configure the Git Integration to use GitLab on-premises (Beta)
Configure the Git integration for self-managed GitLab.
The Git Integration has beta support for a self-managed GitLab installation deployed on-premises or in the cloud. SnapLogic provides an app gateway, a secure transparent proxy, to route Git requests through your Groundplex to the GitLab server, providing an additional layer of security.
To enable use of self-managed GitLab for tracking SnapLogic assets, you need the following:
- A subscription for the SnapLogic Git Integration
- Administrative permission for the GitLab group
- SnapLogic Environment (Org) admin permission
Repository visibility
We recommend that you configure the Git Integration to only access repositories dedicated to SnapLogic assets. This improves the performance of authorization and Git operations in the SnapLogic Platform. It also improves usability by reducing the list of repositories that pipeline developers must choose from during checkout.
- comma-separated list
- group_name/* means all the repositories right under the root, not in subgroups.
- group_name/** means the whole tree
- group_name/subgroup_1/*, group_name/subgroup_1/subgroup_2/* or _name/subgroup_1/subgroup_2/…/subgroup_n/* means all the repositories under the subgroup_1, subgroup_2 or subgroup_n.
- group_name/subgroup_1/**, group_name/subgroup_1/subgroup_2/**, group_name/subgroup_1/subgroup_2/…/subgroup_n/** means all the repositories under the subgroup_1, subgroup_2, or subgroup_n and their descendants subgroups. Here, the first case covers all the others.
- group_name/repositorya, group_name/subgroup_1/repositoryb, group_name/subgroup_1/repositoryc, group_name/subgroup_1/subgroup_2/repositoryd or group_name/subgroup_1/subgroup_2/…/subgroup_n/repositorye means the specific repositories listed: repositorya, repositoryb, repositoryc, repositoryd, and repositorye.
Create an application in GitLab
To enable GitLab to track SnapLogic assets, create an application that configures connectivity:
- Log in to GitLab.
- Navigate to your Group.
- Select Settings.
- Click Applications.
- Click Add a new application.
- Enter a name.
- Specify these values:
- For Redirect URI, enter:
https://control-plane-name.snaplogic.com/api/1/rest/asset/app/oauthcallbackwherecontrol-plane-nameis the control plane you are using. For example:- elastic
- uat
- emea
Important: This Redirect URI is the same as the Callback URL that you specify to configure the Git Integration in your SnapLogic environment/org. - Leave the Confidential box checked.
- For Scopes select the following:
- api
- read_api
- read_user
- write_repository
- Click Save application.
- Click the application to view it and copy the secret to use when configuring the SnapLogic environment.
- For Redirect URI, enter:
Configure the SnapLogic environment
To complete the configuration, the SnapLogic Environment Admin can configure Git Integration settings in Admin Manager as follows:
- Open Admin Manager.
- From the left navigation panel under System Configurations select Git Integration.
- From the Git integration type dropdown list, select GitLab on-premises. The configuration page opens:
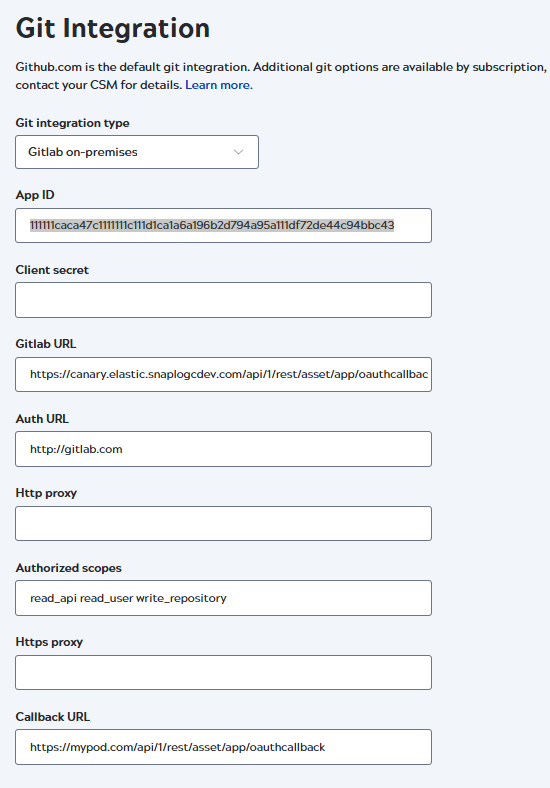
- Enter the following values:
- App ID: The Application ID from the GitLab application.
- Namespaces: An optional, comma-separated list of repository paths that specifies which repositories are visible to developers in the SnapLogic interface. Refer to Repository visibility for the acceptable syntax.
- Client secret: The secret copied from the GitLab application.
- Gitlab URL: The app gateway URL in the format:
org-location-environment-appname.control-plane-name:port-number.
- Value:
http://org-location-environment-appname.controlplanename:port
where:
- org: The environment name.
- location: The location of your Groundplex. Always
sidekick. - environment: The value in the Environment field in your Groundplex Snaplex Settings tab.
- appname: gitlab.
- controlplanename: The control plane that hosts
your environment and the app gateway port number:
- Production:
appgateway.prod.snaplogic.io:8095 - UAT:
appgateway.uat.snaplogic.io:8095 - EMEA:
appgateway.emea.snaplogic.io:8095
- Production:
-
For example, with an environment (Org) named
testand a Groundplex with an Environment value ofdev, the gateway URL for self-managed GitLab would be as follows:http://test-sidekick-dev-gitlab.appgateway.prod.snaplogic.io:8095
If your environment values have any special characters or spaces, then the characters must be removed when specifying the gateway URL string.
For example, with an Environment (Org) named as
test-12with an Environment value ofdev-12, the gateway URL would be updated as follows:http://test12-sidekick-dev12-gitlab.appgateway.prod.snaplogic.io:8095
Attention: The original values on the Org and Environment can be retained. This change is only required for the App gateway URL string.
- Value:
http://org-location-environment-appname.controlplanename:port
where:
- Auth URL: The URL for your Git Lab server.
- Authorized scopes:
apiread_apiread_userwrite_repository - Callback URL: The Redirect URI from
the GitLab application,
https://control-plane-name.snaplogic.com/api/1/rest/asset/app/oauthcallback.Where control-plane-name is the control plane you are using. For example:- elastic
- uat
- emea
Important: This Callback URL is the same as the Redirect URI that you specified in the GitLab application.
- Click Save.
- Open Project Manager.
- From the left panel select Settings.
- Scroll down to Git Integration and click Configure Git.
- From the Git Integration Type dropdown list, select GitLab on-premises.
The configuration dialog opens:
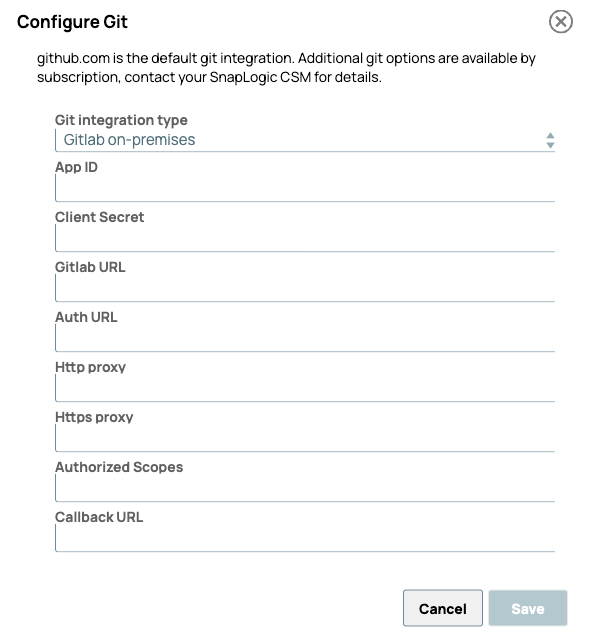
- Enter the following values:
- App ID: The Application ID from the GitLab application.
- Namespaces: An optional, comma-separated list of repository paths that specifies which repositories are visible to developers in the SnapLogic interface. Refer to Repository visibility for the acceptable syntax.
- Client Secret: The Secret copied from the GitLab application.
- GitLab URL: The app gateway URL in the format:
org-location-environment-appname.control-plane-name.
- Value:
http://org-location-environment-appname.controlplanename:port where:- org: The environment name.
- location: The location of your Groundplex. Always
sidekick. - environment: The value in the Environment field in your Groundplex Snaplex Settings tab.
- appname: gitlab.
- controlplanename: The control plane that hosts your
environment and the app gateway port number:
- Production:
appgateway.prod.snaplogic.io:8095 - UAT:
appgateway.uat.snaplogic.io:8095 - EMEA:
appgateway.emea.snaplogic.io:8095
- Production:
- Value:
- Auth URL: The URL for your GitLab server.
- Authorized scopes:
apiread_apiread_userwrite_repository - Callback URL: The Redirect URI from
the GitLab application,
https://control-plane-name.snaplogic.com/api/1/rest/asset/app/oauthcallback.Where control-plane-name is the control plane you are using. For example:- elastic
- uat
- emea
Important: This Callback URL is the same as the Redirect URI that you specified in the GitLab application.
- Click Save.
Configure the Groundplex
Configure the Groundplex to connect to the app gateway in Admin Manager.
- In the left pane, click Snaplexes.
- Click the Groundplex to open the Update Snaplex page.
- Click the Node properties tab.
- In the Global properties section, click + Add new global property to add the gateway key-value pair:
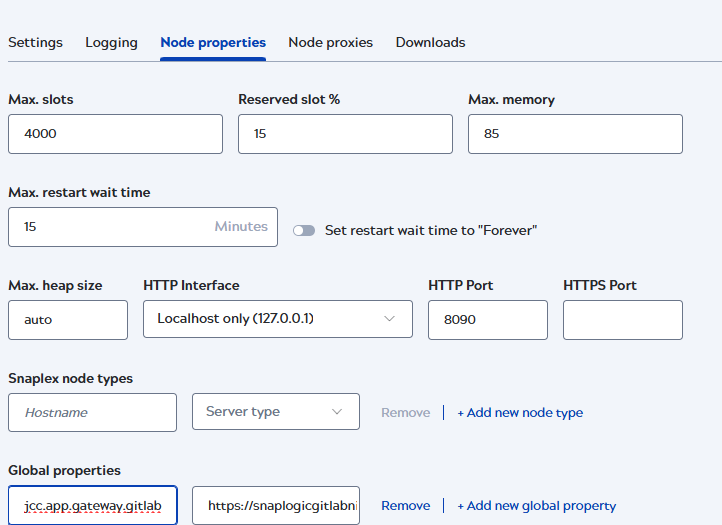
- Enter the appropriate values for the app gateway:
- Key:
jcc.app.gateway.gitlab - Value: Example: https://snaplogicgitlab.nia.snaplogic.com
- Key:


