Snaplex configuration settings for Snaps
In SnapLogic Platform, configuring settings on a Snaplex for Snaps controls how, where, and under what conditions Snaps (the building blocks of pipelines) execute. You can add various configuration options or update the existing values in the Node Properties tab on the Update Snaplex dialog in SnapLogic Manager.
These are Java system properties, so you must configure them with the -D
option. For example, jcc.jvm_options = -DSFTP_TIMEOUT_MILLIS=20000
-DSFTP_CONNECTION_RETRY=5 -DSFTP_RETRY_DELAY_MILLIS=1000
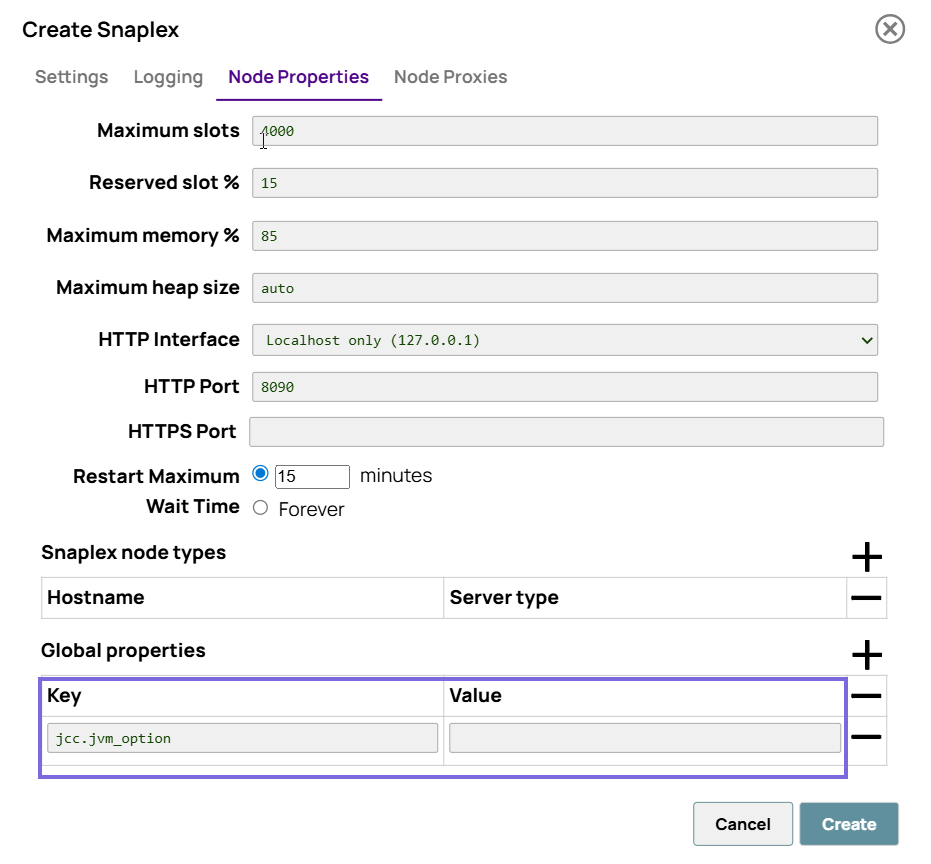
jcc.jvm_options entry in global properties, the
JCC needs to be restarted for the change to take effect. 

