Accounts
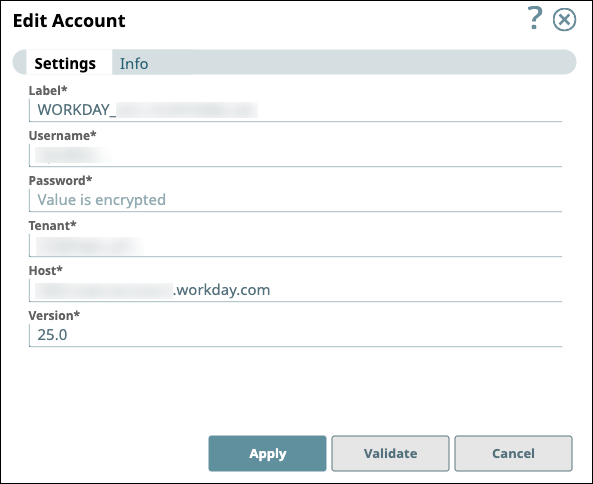
SnapLogic accounts provide the information that Snaps need to access source and target endpoints when executing. For example, a MySQL Snap requires authenticated access to a MySQL database. In SnapLogic Platform, you create an account to store credentials and any other information necessary to connect, such as a URL, hostname, and port number.
Protection for account information
At runtime, account credentials are protected as follows:
-
For a SnapLogic-managed Snaplex (Cloudplex), when you create an account, the information in it is encrypted by the browser before transmission using your Org’s public key. At rest, the encrypted account data is stored in an encrypted Amazon S3 bucket. When a pipeline executes, the Snaplex decrypts the information using a private key.
-
For a self-managed Snaplex (Groundplex) the default behavior is the same as for a SnapLogic-managed Snaplex. Organizations can add one of the following for additional security:
-
Enhanced Encryption: Organization creates and manages the private keys used by nodes to decrypt credentials.
-
Secrets Management: Organizations with a third-party secret manager, such as HashiCorp Vault.
-
Create accounts and control access
You can create accounts from Project Manager or add a new account when configuring a Snap. For some endpoints, SnapLogic supports different types of accounts. For example, for SQL Server, you can choose between a regular or a dynamic account. Dynamic accounts offer expression-enabled fields as described in the next section.
A single account can be used by multiple pipelines, Snaps, and flows. Accounts are accessible to the user who created them and to pipelines in the Project folder in which they were created. Accounts in a shared folder can be used by anyone with access permission to that folder. Org admins with access to multiple Orgs can migrate accounts from one Org to another.
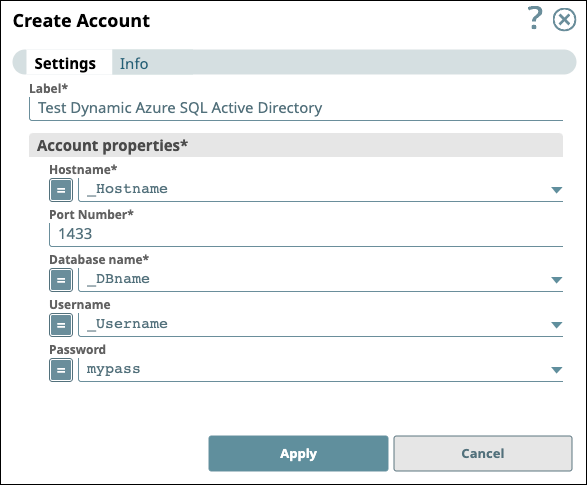
Dynamic accounts
Dynamic accounts can use expressions for connection information instead of literal values. You can then define the values as pipeline parameters, or if your Org is using Secrets Management, provide the values necessary to fetch credentials from a Secrets Manager.
To change a field to be dynamic, click and enter the expression value. If you change a field with an encrypted value, such as a password or a token, to use an expression, the IIP clears the original value to protect sensitive information.