Secrets Management with Azure Key Vault
SnapLogic Secrets Management supports the Azure Key Vault secrets manager to securely store your endpoint credentials.
SnapLogic Secrets Management supports the Azure Key Vault secrets manager to securely store your endpoint credentials. Using Secrets Management with Azure Key Vault requires:
- One or more Groundplex nodes in the Azure cloud environment configured as managed identities.
- An Azure Key Vault configured with IAM roles that are assigned to the Groundplex managed identities.
- Snap accounts configured with expression-enabled credential fields to access the secrets.
Important: Although Azure Key Vault can store API keys, encryption keys, and certificates,
Secrets Management only supports accessing tokens and passwords for endpoint credentials.
The following illustrates how SnapLogic Secrets Management works with Azure Key Vault.
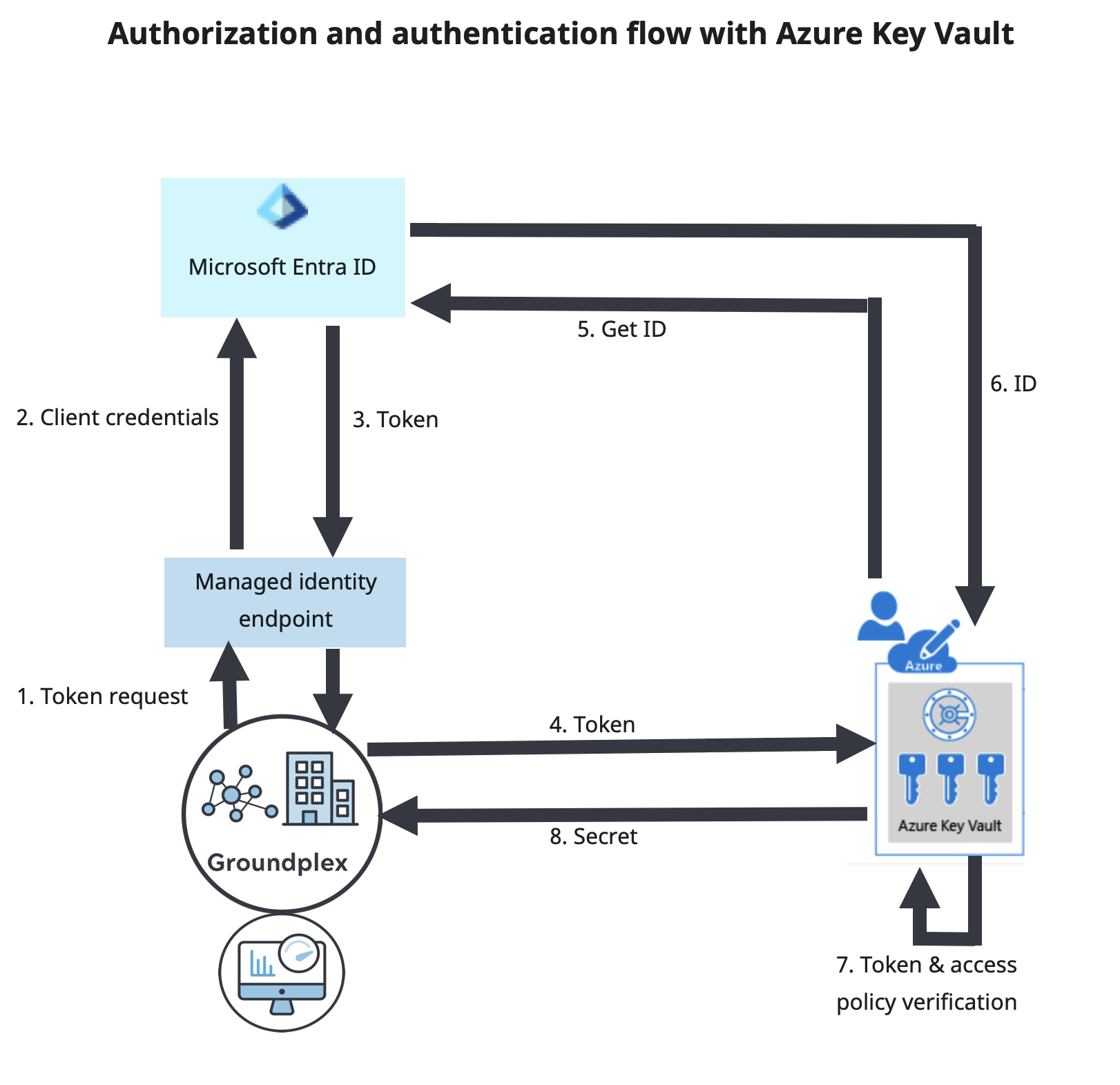
The authorization and authentication flow includes:
- As a managed identity, the Groundplex node requests a token from Microsoft Entra ID by passing in its client ID.
- Entra ID returns a token that the Groundplex node passes to Azure Key Vault with the request for the secret.
- Azure Key Vault checks the Groundplex ID with Entra ID and verifies the token and access policy defined in the IAM role before returning the secret.
To use Azure Key Vault as your secrets manager:


