Configuring Cross Account IAM Role Support
The Cross-Account IAM Role enables a client from an AWS account to access the resources of another AWS account temporarily using the Snaps that support Cross IAM role functionality. This helps organizations or different teams in an organization to access each other's AWS accounts without compromising security by sharing AWS credentials.
You can briefly allow access to your AWS account and specify the access duration. You must create a role and policy in your AWS account. The policy created by the host is attached to the access seeker's account. This Cross-Account IAM role enables SnapLogic to trigger the necessary APIs.
Prerequisites
-
Familiarity with the SnapLogic and AWS platforms.
-
AWS Account with S3 buckets.
Key Steps
Create a cross-account IAM role and policy in AWS Account
- Obtain the account ID for the AWS account used by the S3 Snap. View AWS account identifiers - AWS Account Management explains how to find the ID.
- Log in to the AWS Management Console with the trusting account, the one that controls the S3 bucket.
- In the console, navigate to .
-
Click .
- Specify the ID for the trusted Snap account that will use this role in the
Account ID field:
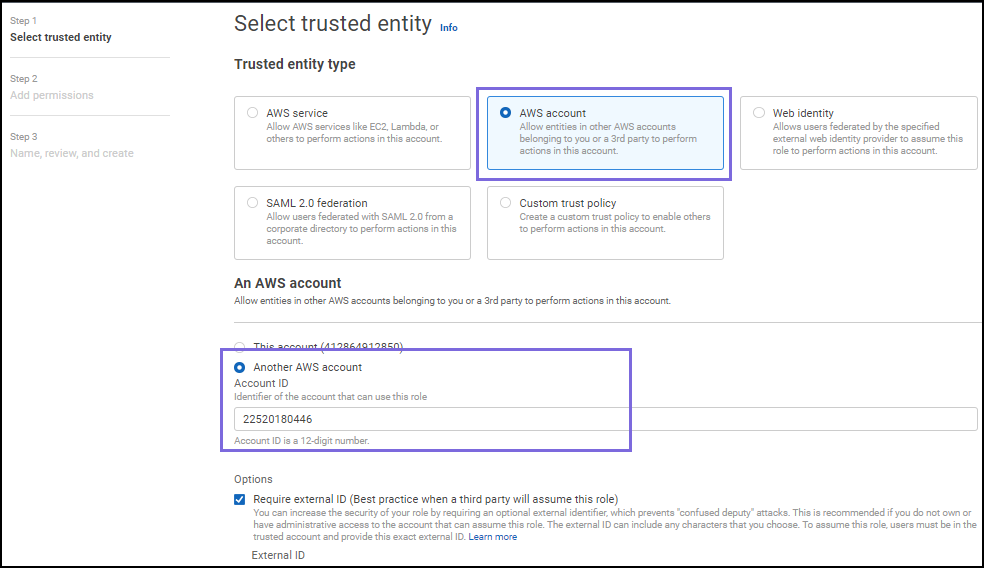
Optionally, require an additional ID for each login by checking the Require external ID checkbox.
-
Click Next: Permissions. When the Attach permission policies screen displays where you can set the permissions, select the checkbox next to the applicable policy for this role.
-
Optionally, as appropriate add tags. Click Next: Tags to skip to the next screen.
-
-
Click Next: Review to skip to the next screen.
-
Review the information displayed and add a name for the role. Click Create role.
-
From the Summary tab, copy the Role ARN. You need this value to associate the policy with the role.
Learn more at What is IAM? - AWS Identity and Access Management
The following shows an example JSON role definition where the Require external
ID was checked and the additional ID is snaplogic.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "sts:AssumeRole",
"Principal": {
"AWS": "222520180446"
},
"Condition": {
"StringEquals": {
"sts:ExternalId": "snaplogic"
}
}
}
]
}
Associate the IAM policy with the role
The policy defines the AWS resources that the role can access.
-
In the AWS console, click Users and select the user name for the trusting account.
-
On the Summary screen, select the desired user and click Add inline policy to attach the policy.
-
Click the JSON tab and enter the details of the policy in the editor, and Click Review Policy.
-
Review the policy summary. Add a name and, optionally, a description for this policy, and click Create policy.
The policy is created and can now be assigned to the cross-account IAM role.
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Action": "sts:AssumeRole", "Resource": "<Role ARN>" } ] }
The Role ARN is displayed on the summary tab when the role is created.
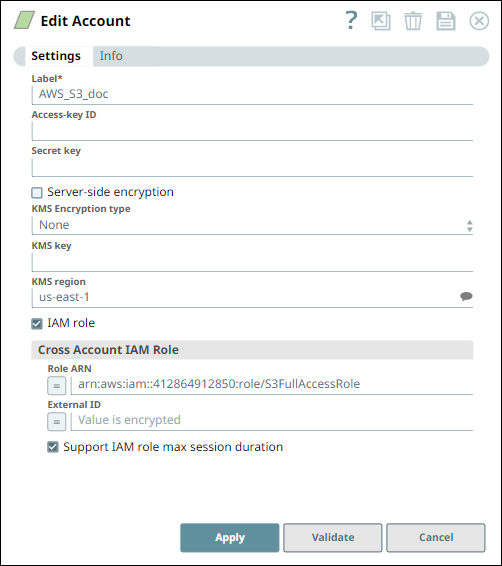
Account settings for cross-account access
You can configure the cross-account IAM role for an S3 Account or S3 Dynamic Account. You will need the Role ARN and External ID (if set up in the role) from the trusting S3 account.
-
In the S3 Account, select the IAM role check box.
-
Specify the Role ARN and External ID provided by the S3 host account: