Authenticate using JSON Web Token (JWT)
Authenticate using JSON Web Token (JWT)
SnapLogic Public APIs now accept JSON Web Tokens (JWTs) for authentication and provide the following benefits:
- They avoid the need to pass the username and password in the authorization header.
- They ensure data integrity and prevent tampering because any modification invalidates the token.
- Your organization can use your choice of Identity Providers (IdPs), open source libraries, or token generators.
The JWT tab on the Admin Manager Authentication page includes configuration fields for enabling JWT-based authentication. You can configure public APIs to support both Basic Authentication and JWTs, or restrict access to JWTs only.
Authorization: Basic fails with an
HTTP 403 error. This applies across all Orgs/Users. If both
the Basic and JWT are enabled for authentication, you can use both options for
Public APIs just by changing the authentication method.- Create an OKTA based token
- Use the Token to run the API
- From Admin Manager select JWT as the authentication method. For detailed information to configure JWT refer to JWT authentication.
Example
Setting up JWT (JSON Web Token) for OKTA involves configuring OKTA to issue and validate JWT tokens for secure authentication.
Organizational requirements
Your organization must have the following elements configured:
- An active user account must exist within your organization's identity management system.
- The user account must have appropriate permissions to access the API resources.
- Your organization must have OAuth or OpenID Connect (OIDC) capabilities enabled.
- The authentication application (such as Okta or Microsoft Azure AD) must be properly configured and accessible.
Technical prerequisites
- Access to your organization's admin console with appropriate administrative privileges.
- An API client tool such as Postman for testing and implementing the authentication.
- The base URL for your API endpoints.
- Knowledge of which APIs require JWT authentication versus basic authentication.
Important: If your organization has already configured JWT authentication applications, you may not need to create new ones.
Configure JWT authorization settings
The Okta Admin console helps to manage the JWT authentication settings. Follow these detailed steps to access and navigate the console:
- Navigate to your organization's Okta Admin console URL in your web browser.
- Click the Sign in button on the login page.
- Enter your administrative credentials and click the Sign in button to proceed to the next authentication step.
- When prompted, enter the answer to your configured security question.
- Click the Verify button to complete the authentication process.
Obtain the Authorization code
- In your JWT configuration documentation or settings page, locate
the authorization URL under your JWT application (For example in the image
provided below JWT Testing is the application.)
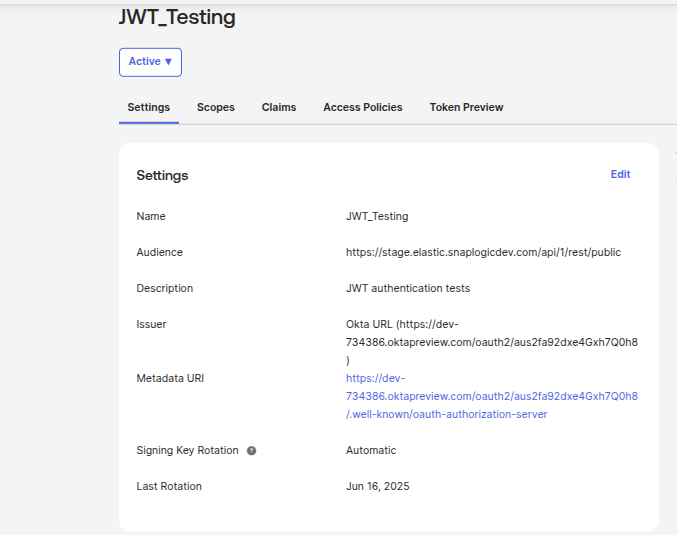
- Click the authorization URL link to initiate the OAuth flow.
- The system redirects you to an authorization page and generate a code in the URL.
- Copy the authorization code from the URL in your browser's address bar - this code appears as a parameter after code=
- Enter your app's details and callback URLs.
- To add custom claims in your JWT, create a custom authorization
server.
- Click on Add Authorization Server.
- Provide name and audience for the server.
- Configure Scopes,
Claims, and Access
Policies within your Authorization Server.
- The username in SnapLogic should be the content of the SUB claim. For IdPs which cannot be modified send a custom claim named snaplogic_username containing the username in Snaplogic.
Test the JWT token
- Authentication: Send a POST request with login credentials to the authentication endpoint to obtain a JWT.
- The application in the authentication has a unique id and this code helps to
generate the bearer token. The sample URL is as follows:
POST https://dev-734386-admin.oktapreview.com/admin/oauth2/as/aus2fa92dxe4Gxh7Q0h8
- Use the JWT for subsequent requests:
- Use the retrieved Token in the
Authorizationheader of subsequent API requests.Authorization: Bearer <token>
- Use the retrieved Token in the
- Test Your JWT Authentication
- Test your endpoints by sending requests with the JWT in the
Authorizationheader. - Use Postman to retrieve the details of the user
- Test your endpoints by sending requests with the JWT in the
Response
A successful response includes a Code 200 OK.


