Kafka SSL Account
Overview
You can use the Kafka account type to connect Confluent Kafka Snaps with data sources that use Kafka SSL accounts.
Prerequisites
- None
Limitations and known issues
None.
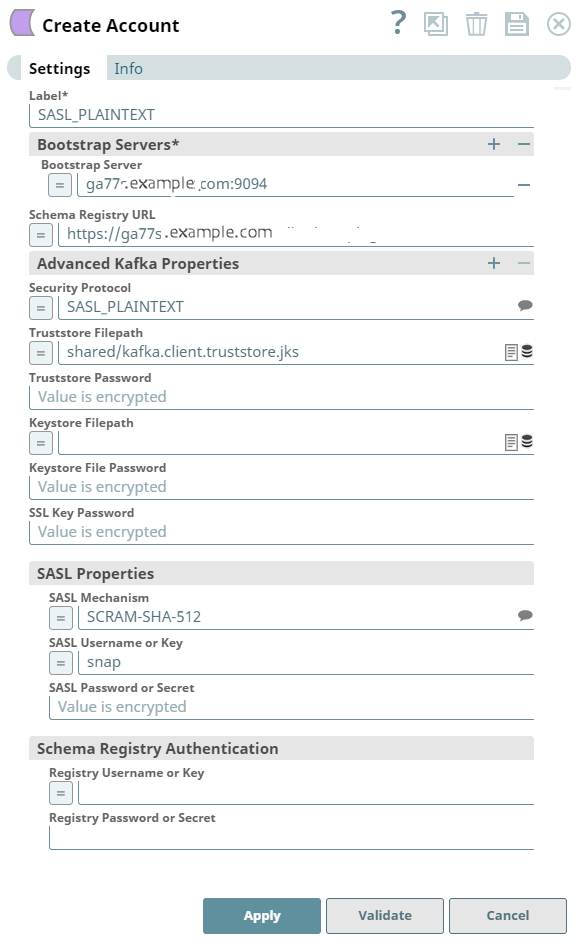
Account settings
- Expression icon (
): Allows using JavaScript syntax to access SnapLogic Expressions to set field values dynamically (if enabled). If disabled, you can provide a static value. Learn more.
- SnapGPT (
): Generates SnapLogic Expressions based on natural language using SnapGPT. Learn more.
- Suggestion icon (
): Populates a list of values dynamically based on your Snap configuration. You can select only one attribute at a time using the icon. Type into the field if it supports a comma-separated list of values.
- Upload
 : Uploads files. Learn more.
: Uploads files. Learn more.
| Field / Field set | Type | Description |
|---|---|---|
| Label | String |
Required. Specify a unique label for the account.
Default value: N/A Example: Kafka SSL Account |
| Bootstrap Servers | Use this field set to configure a list of Bootstrap servers. | |
| Bootstrap Server | String/Expression |
Specify the host:port pairs to be used for establishing the initial connection to the Kafka cluster.
Default value: N/A Example: ec2-55-334-44-55.compute-1.amazonaws.com:9000 |
| Schema Registry URL | String/Expression |
Specify the schema registry server URL.
Default value: N/A Example: http://ec2-55-334-44-58.compute-1.amazonaws.com:8000 |
| Advanced Kafka Properties | Use this field set to
specify any additional Kafka properties for connecting to the Kafka
server that are not explicitly provided in the Confluent Kafka
Snaps. Note:
|
|
| Key | String/Expression |
Specify the key for any Kafka parameters that are not explicitly supported by the Snaps.
Default value: N/A Example: Customer2 |
| Value | Integer/Expression |
Specify the value for the corresponding key that is not explicitly supported by the Snaps.
Default value: N/A Example: 600 |
| Security Protocol | String/Expression/ Suggestion | Select the security protocol from the drop-down list. The
available options are:
Default value: SSL Example: SASL_PLAINTEXT |
| Truststore Filepath | String/Expression | Select the location of the Truststore file that is used to
authenticate the server. Default value: N/A Example: kafka.net.ssl.truststore |
| Truststore Password | String/Expression |
Specify the password for the Truststore file.
Default value: N/A Example: test1234 |
| Keystore Filepath | String |
Select the location of the Keystore filepath of the client.
Default value: N/A Example: :\var\private\ssl\kafka.client.keystore.jks |
| Keystore File Password | String/Expression |
Specify the Keystore password to access the Keystore file that is used for client authentication. The keystore file contains the private key of the certificate; hence, it needs to be secure.
Default value: N/A Example: d$ra0W$$#p!9 |
| SSL Key Password | String |
Specify the SSL password of the private key in the SSL key store file.
Default value: N/A Example: password3 |
| SASL Properties | Use this field set to specify the account properties that are used for the security protocols. | |
| SASL Mechanism | String/Expression/ Suggestion | Select the SASL authentication mechanism for the account from
the list. The available options are:
Default value: PLAIN Example: SCRAM-SHA-512 |
| SASL Username or Key | String/Expression | Activates when you select SASL_SSL or SASL_PLAINTEXT for Security
Protocol. Specify the username for the SASL security protocol. To connect to Confluent Cloud, enter the API Key. To set up an account for Confluent Cloud:
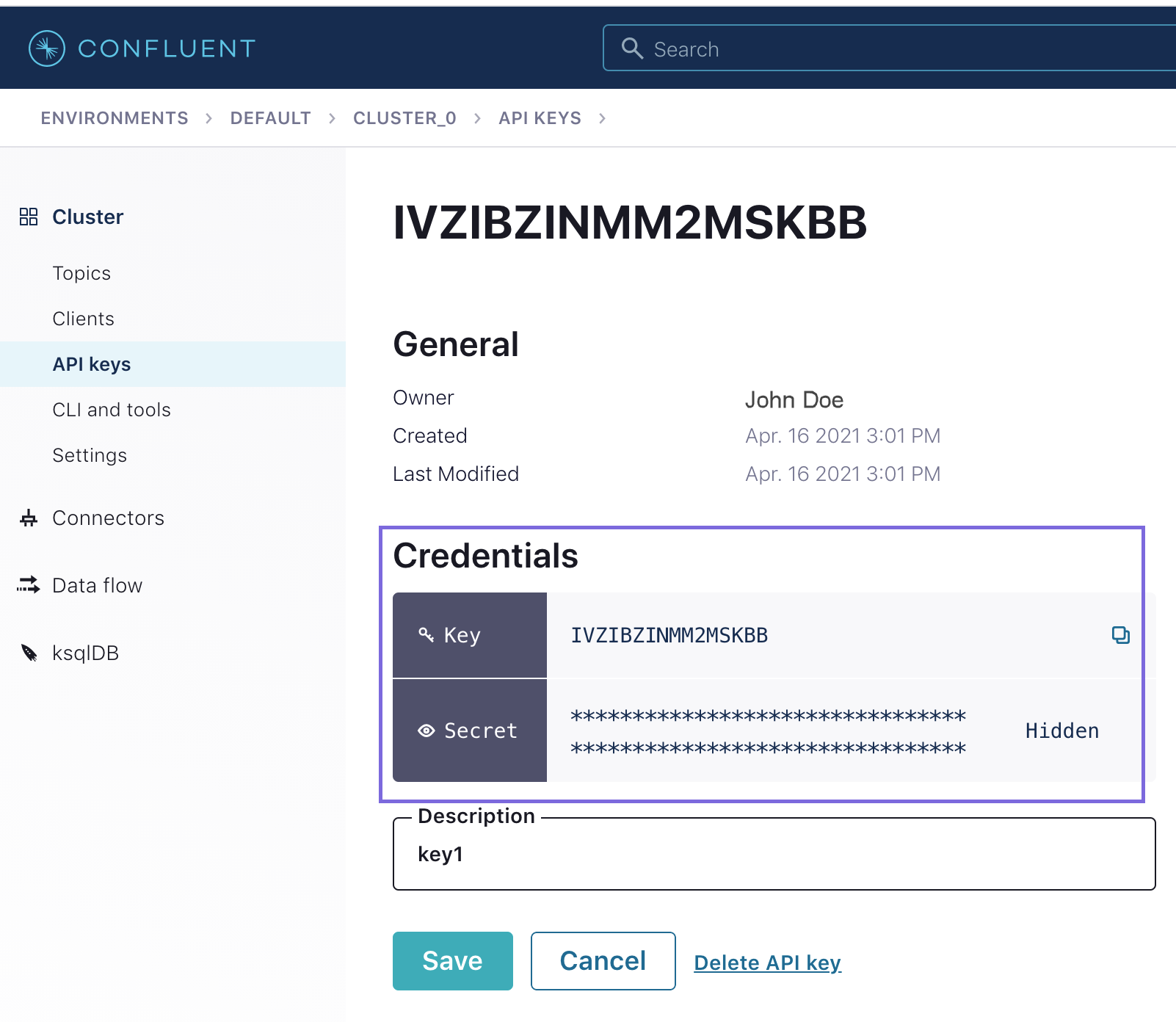 Default value: N/A Example: Admin |
| SASL Password or Secret | String | Activates when you select SASL_SSL or SASL_PLAINTEXT for
Security Protocol. Specify the password for the SASL security
protocol. To connect to Confluent Cloud, enter the API Secret obtained from the Confluent Control Center. Default value: N/A Example: password4 |
| Schema Registry Authentication | Use this field set to
specify the Registry Username and Password in case the Schema
Registry requires authentication. If you are using Avro data type,
the Schema Registry URL and Schema Registry Authentication values
must be provided as advised by the Confluent Control Center. 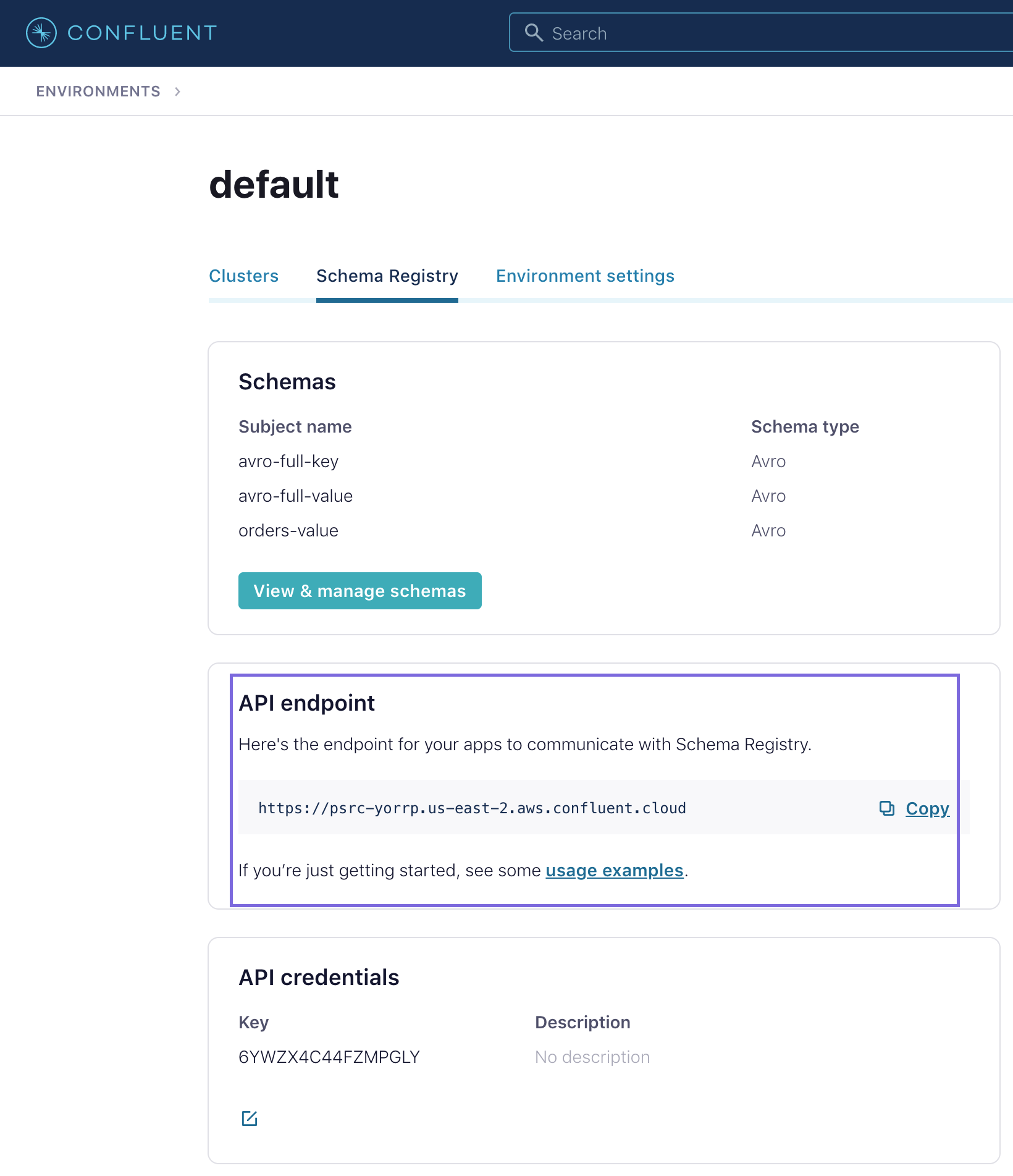 |
|
| Registry Username or Key | String/Expression |
Specify the username or key for schema registry authentication.
Default value: N/A Example: transactions-key |
| Registry Password or Secret | String/Expression |
Specify the password or secret for schema registry authentication.
Default value: N/A Example: tr@nS@xt-001 |


