Snaplex Configuration Settings for Snaps
SFTP Connections
You can configure the following SFTP (Secure File Transfer Protocol) settings in the global.properties file.
These are used when using SFTP protocol with File read/write/browse type Snaps.
They are Java system properties, so they need to be defined with the -D option.
-
sftpSessionTimeoutSec: The session objects are stored in the internal cache of the Snaplex node for up to the value in seconds of this property. When the SFTP file protocol is used in any Binary Snap, the session cache is examined and, if any session has been idling for longer than this property value, the session object is closed and removed from the cache. The default value is 3600. -
cacheSftpSessions: IfcacheSftpSessionsis False, the SFTP session object is closed and removed from the cache if no SFTP channel is connected in the session. Otherwise, the session objects remain in the cache with up to the value in seconds of thesftpSessionTimeoutSecglobal property. The default value is True. -
maxSftpChannels: The maximum number of concurrent channels open per session (default value is 1). You can obtain the correct value to specify formaxSftpChannelsfrom your SFTP server administrative settings. In the SFTP file protocol, SFTP connection consists of a session and a channel. When an SFTP client (for example, Binary Snap) establishes a TCP connection with a server, it is called a session, while a channel is simply a virtual connection within a single session. Typically, multiple concurrent channels can be opened in each session. You can use each channel to perform a read/write/get command. The maximum number of concurrent sessions per client IP address is also limited by the SFTP server settings. For example, if the maximum number of sessions allowed is 8 andmaxSftpChannelsis set to 8, then up to 64 requests can be processed by the SFTP server concurrently. IfmaxSftpChannelsis not specified, then its default value is 1, which allows a maximum of 8 concurrent requests to be processed. One Binary Snap can use more than one channel. enableJschLogger: Whether to enable extra logging from SFTP (default value is False)SFTP_TIMEOUT_MILLIS: The number of milliseconds to wait for an SFTP connection to be established (default value is 30000)SFTP_CONNECTION_RETRY: The number of times to retry a connection (default value is 3)SFTP_RETRY_DELAY_MILLIS: The delay between retries, in milliseconds (default value is 1000)ftpsDelayBeforeClosing: Set to 1 or more if an FTPS file is truncated after being written by a File Writer Snap without any error. The default value is 0, and the time unit is in seconds.-
ftpDelayBeforeClosing: Set to 1 or more if an FTPS file is truncated after being written by a File Writer Snap without any error. The default value is 1, and the time unit is in seconds.
jcc.jvm_options entry in global.properties, the JCC needs to be restarted for the change to take effect.
For example, to reduce the amount of time the connection attempt is retried, add the following:
jcc.jvm_options = -DSFTP_TIMEOUT_MILLIS=20000 -DSFTP_CONNECTION_RETRY=5 -DSFTP_RETRY_DELAY_MILLIS=1000The following table lists the new properties supported as of the 4.33 GA release.
| Value | What it does |
|---|---|
-Dsftp.kex=<algorithm(s)> |
Appends to the client’s (SnapLogic’s) acceptable kex (key exchange algorithms) list for the connection negotiation to the SFTP server.
Example: |
-Dsftp.server_host_key=<algorithm(s)> |
Appends to the client’s (SnapLogic’s) supported server_host_key algorithms list for the connection negotiation to the SFTP server.
Example: |
-Dsftp.client_pubkey=<algorithm(s)> |
Appends to the client’s (SnapLogic’s) supported PubkeyAcceptedAlgorithms list for the connection negotiation to the SFTP server.
Example: |
-Dsftp.cipher=<algorithm(s)> |
Appends to the client’s (SnapLogic’s) supported cipher algorithms list for both s2c (server to client) and c2s (client to server) for the connection negotiation to the SFTP server.
Example: |
-Dsftp.mac=<algorithm(s)> |
Appends to the client’s (SnapLogic’s) supported mac algorithms list for both s2c (server to client) and c2s (client to server) for the connection negotiation to the SFTP server.
Example: |
-Dsftp.check_ciphers=<algorithm(s)> |
Appends to the client’s (SnapLogic’s) supported CheckCiphers list for the connection negotiation to the SFTP server.
Example: |
-Dsftp.check_kexes=<algorithm(s)> |
Appends to the client’s (SnapLogic’s) supported CheckKexes list for the connection negotiation to the SFTP server.
Example: |
-Dsftp.check_signatures=<algorithm(s)> |
Appends to the client’s (SnapLogic’s) supported CheckSignatures list for the connection negotiation to the SFTP server.
Example: |
-Dsftp.check_macs=<algorithm(s)> |
Appends to the client’s (SnapLogic’s) supported CheckMacs list for the connection negotiation to the SFTP server.
Example: |
Troubleshooting
If you experience any connectivity issues with your SFTP connection, it might be due to the use of the deprecated algorithms. You can address such exceptions based on their cause, as follows:
| Exception Cause | Resolution |
|---|---|
|
Caused by: com.jcraft.jsch.JSchAlgoNegoFailException: Algorithm negotiation fail:
algorithmName="server_host_key" jschProposal="ssh-ed25519,ecdsa-sha2-
nistp256,ecdsa-sha2-nistp384,ecdsa-sha2-nistp521,rsa-sha2-512,rsa-sha2-256"
serverProposal="ssh-rsa"
|
Set the following properties in your node:
|
|
Caused by: com.jcraft.jsch.JSchAlgoNegoFailException: Algorithm negotiation fail:
algorithmName="kex" jschProposal="curve25519-sha256,curve25519
[email protected],ecdh-sha2-nistp256,ecdh-sha2-nistp384,ecdh-sha2-nistp521,diffie-
hellman-group-exchange-sha256,diffie-hellman-group16-sha512,diffie-hellman-
group18-sha512,diffie-hellman-group14-sha256,ext-info-c" serverProposal="diffie-
hellman-group14-sha1,diffie-hellman-group-exchange-sha1,diffie-hellman-group1-sha1"
|
Set the following properties in your node: -Dsftp.kex=diffie-hellman-group14-sha1,diffie-hellman-group-exchange-sha1,diffie-hellman-group1-sha1
|
Access Token Timeout Settings for Salesforce
The expiration timeout (or session timeout) in Salesforce is 14 minutes by default. To change this value:
- Navigate to and click the Snaplex on which you want to execute the Pipeline containing the Salesforce Snap. The Update Snaplex popup window appears.
-
Click Node Properties and, at the bottom of the tab that appears, add the following entry into the Global properties field set:
jcc.jvm_options = -DSFDC_SESSION_TIMEOUT_MINUTES=<NUMBER_OF_MINUTES>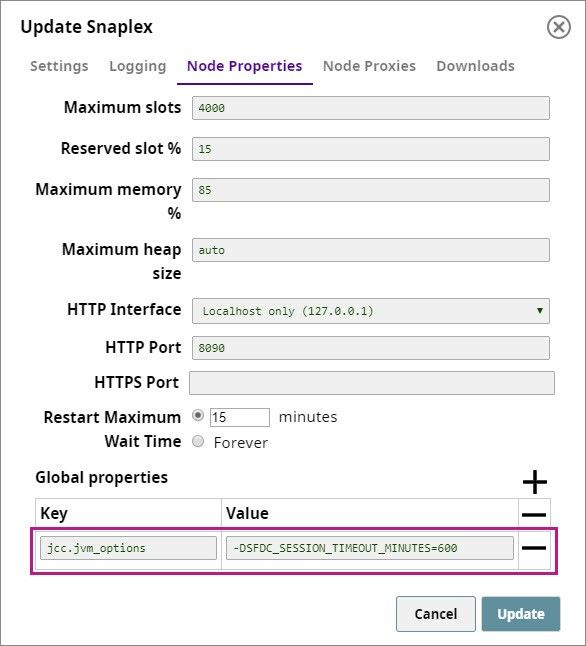
Points to remember:
- The JCC will be restarted.
- The session timeout should be the same or less than the value in the SFDC Web Administration page: .
- SFDC Session Timeout value in the Administration page can be selected between 15 minutes and 12 hours. For more information on working with SFDC timeout settings, see Salesforce Documentation.
- Security token is not mandatory; however, the user can set the Login IP range at the SFDC Account web page to bypass the security token's requirement. Learn more.